Did you know that every time you send an email, it follows a specific ruleset?
These rules allow for email client and server compatibility, ultimately making your email readable. Without at least a cursory understanding of how email protocols work, your email marketing campaigns can fail.
But listen, I understand this can be confusing stuff.
That’s why I’m here to help you demystify various protocols, so let’s go! Mail protocols such as SMTP, POP3, and IMAP play a crucial role in enabling the sending, receiving, and management of emails across different machines, networks, and operating systems.
Table of Contents
Key Takeaways
- IMAP, POP3, and SMTP are the three email protocols. The former two deal with email retrieval, while SMTP is the primary email protocol.
- Understanding how each protocol works, what kinds of protections it offers, and when to use it can propel your email marketing, as you can be confident your messages will reach their intended recipients (and vice-versa).
The Basics of Email Protocols
Let’s expand a bit on the definition from the intro, okay? Email protocols are rulesets emails follow to ensure they reach the intended recipient.
The goals of these protocols are to help us send emails regardless of the operating system, network, and machine we use and to allow us to manage our emails despite the device and email program.
Email protocols are kind of the unsung heroes of digital communication. Without them, we’d be able to send and receive far fewer emails successfully, but if you ask a lot of people what an email protocol is, they probably wouldn’t know, or at least not all of them.
So, let’s change that for you. Here is a list of every email protocol, with detailed overviews of each to come.
- IMAP
- POP3
- SMTP
An Overview of Simple Mail Transfer Protocol (SMTP)
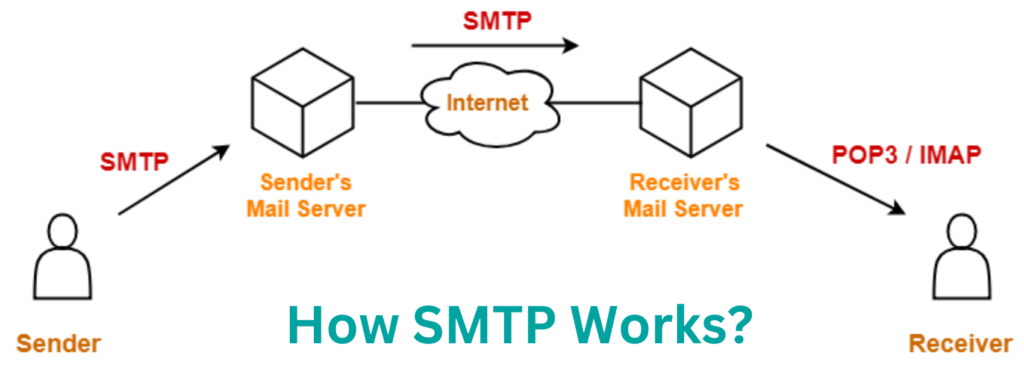
SMTP, short for Simple Mail Transfer Protocol (SMTP), is the backbone of email transmission, enabling email clients like Yahoo Mail, Apple Mail, Outlook, and Gmail to send messages through the internet.
This protocol is crucial for the operation of message transfer agents and mail servers, facilitating the flow of emails from one server to another.
When utilized by an email client, SMTP is responsible for sending messages from the sender’s mail server to the recipient’s email server, whereas IMAP usually retrieves them.
For instance, if you use Gmail to send an email, Gmail’s SMTP server pushes the message to its outgoing mail server, which then establishes a TCP connection to the recipient’s email server on either port 465 or 587, ensuring the email is successfully transferred.
Port what now?
SMTP servers use ports for relaying emails, with the Simple Mail Transfer Protocol SMTP defining how emails are securely transmitted between servers. Initially, SMTP relied exclusively on port 25 for email transmission.
However, due to the need for secure email transmission, the new standard has become port 587, which supports SMTP Secure (SMTPS) encryption.
If not port 587, then it will be port 465 that relays your email. While port 465 can relay SMTPS emails, it’s considered outdated technology and shouldn’t be used over port 587 if an email server has the choice.
An SMTP server is available around the clock to connect to an accessible port and ensure the email reaches the recipient.
Read also: POP3 vs IMAP — Which Email Protocol Is Right for You?
How SMTP works
You prepare your emails as standard, and when you click send, then the real fun begins. The SMTP server receives connection through the Transmission Control Protocol or TCP. Next, the SMTP server sends the email to the correct port.
Mail transfer agents or MTAs will review the sender and recipient’s email addresses to check for domain compatibility. The email will go through either way, but if the domains aren’t the same, there’s an additional step involving a domain name system or DNS server.
The email will land in the DNS server to determine the recipient’s domain and where the email should go.
Then, through POP3 or IMAP, the recipient gets the email.
Interestingly, SMTP can communicate with servers, which is fascinating if you ever see it play out. SMTP commands are crucial in this communication, guiding the interaction between mail clients and SMTP servers.
For example, HELO initiates the conversation by identifying the sender to the server.
MAIL FROM specifies the sender’s email address, and RCPT TO indicates the recipient’s address, setting the stage for the email’s journey.
These commands, along with others like DATA, which signals the start of the message body, are integral to the SMTP conversation, ensuring emails are correctly routed and delivered.
One command the SMTP might send is HELO, which is used for identification. If a mail transaction must be aborted, the SMTP will contact the server with an RSET message. The email data disappears from there.
QUIT tells the server to disconnect from the SMTP, while DATA allows the email data to go between the server and client and land the email in the SMTP server.
MAIL is how the email transfer occurs and can be used to separate one email transaction from another. RCPT is for the replicant email address.
Read also: What Is Simple Mail Transfer Protocol (SMTP)? A Brief Guide
An Overview of Internet Message Access Protocol (IMAP)

Are you still with me after that? Great, because next is IMAP, or Internet Message Access Protocol, commonly called the IMAP protocol.
The IMAP protocol often gets lumped in with POP because they’re both used for email retrieval versus sending. However, they deserve the differentiation, so allow me to provide it.
Unlike POP, the IMAP protocol synchronizes email and stores emails on a remote server. It supports message flags and multiple client access, making it a superior choice for managing emails across various devices.
Email clients will access a mail server via IMAP and a TCP connection. Thanks to IMAP, it doesn’t matter which device you use to check your email, as you can always see it.
For example, if you open your inbox on your work computer, you can go home and check your mail on your personal computer, smartphone, or tablet.
When IMAP was created, it intended to let several email clients manage one email box and let the user delete emails at their discretion.
Like SMTP, IMAP uses ports, but they don’t occupy the same port. Instead, its traditional port is 153. If IMAP operates over TLS or SSL (Secure Sockets Layer), it’s IMAPS instead and uses port 993.
Many email servers and clients use IMAP, including Outlook and Gmail.
Fun facts: Mark Crispin created IMAP in 1986. It was an advanced version of the original POP protocol. However, since the late 1980s, IMAP has undergone several iterations.
First, there was the switch to IMAP2 in 1988, then IMAP3 in 1991, and IMAP2bis for MIME body structure support, which later became IMAP4.
How IMAP works
When an email is incoming to a recipient, it will go to an email server.
The server stores recipient emails until the user checks their email. The emails then stay until the user removes them, facilitating usage for several people in one mailbox.
Importantly, IMAP supports simultaneous access by multiple clients, making it ideal for accessing emails from different locations or devices and for multiple users managing messages in one mailbox.
Read also: 29 Critical SMTP Response Codes And How To Fix Them
POP3 – What’s Popping with This Email Protocol?

IMAP isn’t the only internet protocol with a lengthy history. There’s also POP3, or Post Office Protocol version 3, one of the key mail access protocols.
POP3, as a crucial part of mail access protocols alongside IMAP, facilitates the retrieval of email messages from the server. It relies on an IP network for email retrieval, although its operation differs from IMAP.
Through the IP network, POP3 accesses a mailbox on a mail server, allowing emails to be deleted, retrieved, or listed.
The POP3 clients will retrieve all emails and show them on the client’s device, be it a computer or otherwise, and then remove them from the server. So, why do that?
POP was originally created to support internet users with temporary internet connections like dial-up.
That’s why, when they’re connected to the internet, a user could see their emails and retrieve them, and when offline, they could still view the messages.
Of course, since we’re not living in the dial-up days anymore, POP protocols have caught up.
For example, POP3 clients allow you to leave the emails on the server even after you retrieve them. In that case, you can download the emails identified by a unique ID list command.
POP3 uses port 110. Opportunistic TLS or STLS and POP3S allow encryption, with the latter using SSL or TLS.
So, how did we get to POP3? The first edition of this email protocol, POP1, was created in 1984, and then POP2 in 1985. POP3 followed very soon after in 1988 but has been consistently upgraded with new specifications.
By the way, there is POP4, but it’s only used for message flag management, multipart message support, and folder management.
How POP3 works
POP3 lets internet users access emails kept on a server. It allows the user to download the email and then delete the email operations.
The emails end up on your local device, such as a computer, and not in the remote server, where they can clog up the available space.
This internet protocol also allows for offline and local message retrieval. Plus, you’ll remember that you can configure POP3 to store your emails on the server, where a copy of your email will remain until you remove it.
IMAP vs POP3
The primary difference between these two email protocols is how they store your message.
With IMAP, your emails are stored in a cloud mail server, allowing you to see your emails across devices. Another difference is that IMAP doesn’t delete emails from the server automatically.
What Are Email Authentication Protocols
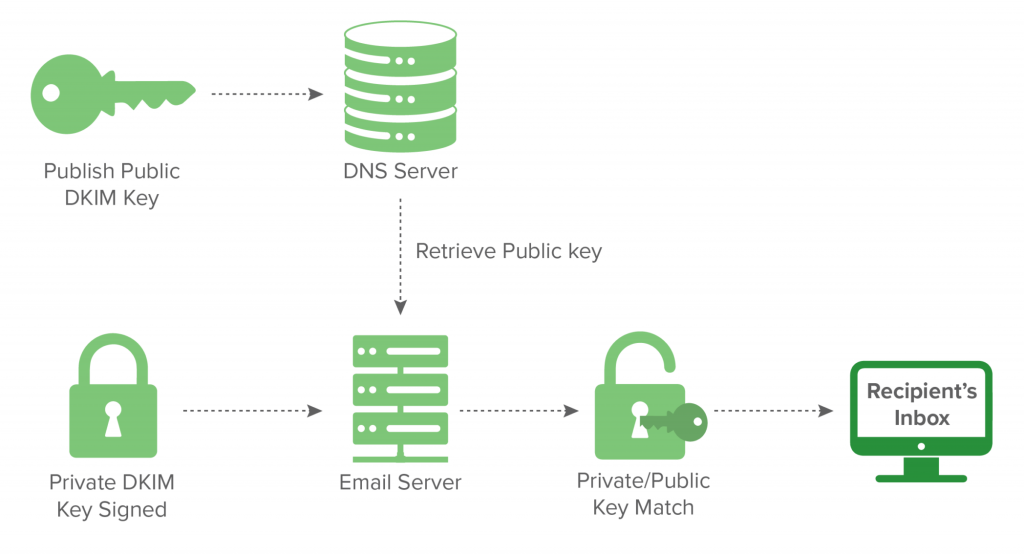
Protocols rely on authentication techniques that validate a sender or recipient’s (or both!) domain(s). They exist to verify identities and combat spam. Let’s review the types of email authentication protocols.
SPF
No, not that SPF. Instead, this version is short for Sender Policy Framework. Under SPF, a mail server sending emails gets permission to use a sender domain.
To do this, it will check the IP address and compare it against approved addresses in its records.
The server that receives the email will then do the same, checking the SPF record to determine whether the email should go through. In some instances, the email might be successfully sent but be flagged.
The goal of SPF is to reduce the number of phishers, scammers, and spoofers on the internet.
Read more: SPF, DKIM, DMARC: Detailed Guide to Email Authentication Protocols
DKIM
Next, there’s DomainKeys Identified Mail, or DKIM for short. This method for authenticating emails requires a digital signature.
The email recipient can use the signature to verify that the domain owner sent the email.
Each signature is attached to a specific domain name. You’ll have to check the DNS for the public key to confirm the information.
DKIM can be combined with other authentication protocols, including SPF and DMARC—which I’ll discuss in just a moment—to make it even more efficient in safeguarding your email account from impersonators, phishers, and other scammers.
DMARC
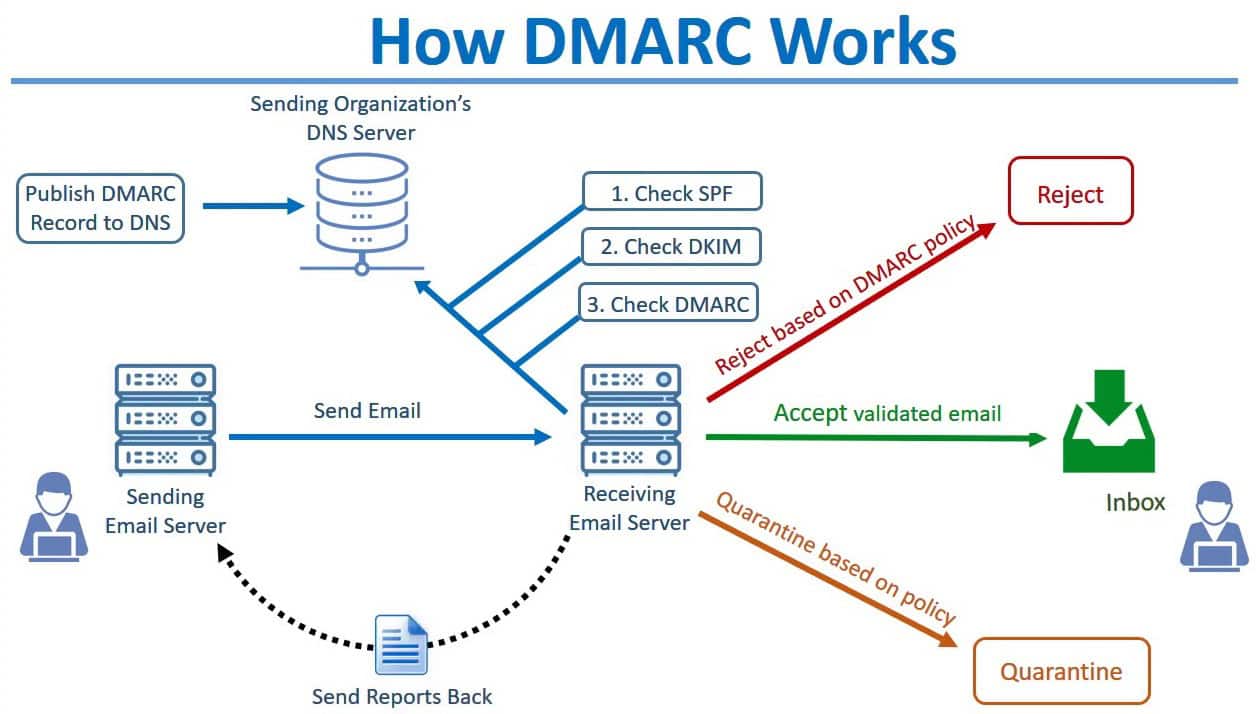
Okay, so what is DMARC?
It stands for Domain-Based Message Authentication. As the name suggests, this email authentication protocol is used for safer emailing.
It takes from DKIM and SPF rules and introduces author links in the domain name.
DMARC DNS entries are published and can be checked based on the domain owner’s instructions.
Only emails that pass DMARC should be delivered, as failing the check means the email could be a phishing or spoofing scheme or another type of cyber threat.
Read also: Email Authentication 101: Cover Your Bases Against Phishing Attacks
Email Protocol Security
Of course, we can’t talk about safety and security when sending and receiving emails without discussing email encryption.
Encryption encodes the contents of an email until the recipient decodes them. The point of encrypting emails is to protect sensitive information from identity thieves and to maintain secure internet access throughout the transmission process.
One way of achieving secure emails is through SSL, and another is TLS.
I’ve mentioned both but not discussed them in much detail, so let’s change that!
Starting with SSL, this encryption protocol was created in 1995. It walked so TLS can run, as that’s the more modern encryption method.
SSL performs a handshake (digitally, of course) to authenticate both devices while also creating a digital data signature attesting to the accuracy and purity of the data (aka, no one’s tampered with it).
Since 1999, it’s been all about TLS, which also encrypts emails or websites, but better than SSL. It, too, uses handshake protocols to ensure the veracity of the devices and creates TLS records.
Read more: Email Authentication 101: Cover Your Bases Against Phishing Attacks
Choosing the Right Protocols for Your Business
Although there’s only one email protocol for sending emails and two for receiving them, it’s still a valid question to ask which protocol is best for your business.
As you mull over your options, consider these tips designed to help.
Business size
As a small business, gravitating more toward IMAP than POP3 makes sense, considering the former will retain the messages received on its server unless and until deletion occurs. You have a small staff, and you won’t fill up the server quite as quickly in your early days.
Email marketing software compatibility
You must also consider how compatible the protocol is with your existing email marketing tools.
Some email clients and servers are built for IMAP, others for POP, and some for both. Depending on which your software supports, you might not get much of a choice in the matter.
Email volume
The larger your email volume, the more space you need, which means POP3 is the more economical solution for you.
Remember to dig into your SMTP port options, as 587 is the more up-to-date port that will ensure your emails go through smoothly (and with encryption!), which is critical when you expand your email volume.
Hosting options
Yet another consideration you must make is which email host you select.
While many are designed to support all three email protocols, even simultaneously, this is another area where the compatibility of the host will dictate which protocol you use for your small business.
Server setup
Lastly, review your server and what it’s set up for. Depending on what takeaways you get from researching the server, you might gravitate more toward IMAP or POP3 protocols going forward.
Remember that when it comes to POP3 and IMAP, you don’t have to choose just one. Your small business can always use both together!
Read also: Everything You Need to Know About Email Subdomains
How to Set Up and Configure Email Protocols
Now that you better understand email protocols, are you eager to set them up on your email service provider of choice? I’ll provide instructions for Gmail, Apple Mail, Yahoo, and Outlook.
How to set up email protocols in Gmail
You can configure SMTP settings by typing in the following:
- SMTP server address – smtp.gmail.com
- SMTP port for SSL – 465
- SMTP port for TLS – 587
- SMTP name – Your first and last name
- SMTP username – Your Gmail email address
- SMTP password – Your Gmail password
If you’re asked to use a secure connection, use authentication, TLS, and SSL, select yes for all.
To turn on IMAP and POP in Gmail, go to Settings, then Forwarding and POP/MAP. The status section will mention whether IMAP and POP are disabled; you can enable one or both. You can also determine what Gmail does with IMAP and POP messages.
:max_bytes(150000):strip_icc()/001-gmail-access-thunderbird-1173150-80fdab9339ec4fb9a6c58965db3b8b7b.jpg)
You’ll have to configure your email client afterward. Gmail provides configuration instructions. Then click Save Changes.
How to set up email protocols in Yahoo Mail
Yahoo only allows you to select POP and IMAP settings. To activate IMAP, you need this information:
- Login info, including your email address and app password
- Outgoing SMTP server data:
- Port 465 or 587
- Smtp.mail.yahoo.com for the server
- Require authentication
- Require SSL
- Incoming IMAP server data:
- Port 993
- Imap.mail.yahoo.com for the server
- Require SSL
You can turn on POP in Yahoo Mail with these settings:
- Login info, including your email address and app password
- Outgoing SMTP server data:
- Port 465 or 587
- Smtp.mail.yahoo.com for the server
- Require authentication
- Require TLS
- Incoming POP server data:
- Port 995
- Pop.mail.yahoo.com for the server
- Require SSL
How to set up email protocols in Outlook
The following manual server settings will connect Outlook with an IMAP or POP-supported email program. The outgoing and ingoing email servers are the same for Outlook, and it also automatically disables POP until you turn it on.

Here’s what you need:
- SMTP encryption – STARTTLS
- SMTP port – 587
- SMTP server – smtp-mail.outlook.com
- POP encryption – TLS
- POP port – 995
- POP server – outlook.office365.com
- IMAP encryption – TLS
- IMAP port – 993
- IMAP server – outlook.office365.com
- Username – Your Outlook email address
- Password – Your Microsoft password
How to set up email protocols in Apple Mail
Apple Mail users can change SMTP settings anytime. If you’re on a Mac, click the Mail app icon, then Mail, and Settings and Accounts. You will see account information on the left, so choose yours.
On the right, you can configure the Server Settings.
The outgoing mail server settings for SMTP are as follows:
- Host name – Mail server name
- Username – Your mail server username
- Password – Your mail server password
- Account – Your mail server account
And here are the incoming mail server settings:
- Host name – Mail server name
- Username – Your mail server username
- Password – Your mail server password
- Account – Your mail server account
Advanced Topics: Ports and Transfers
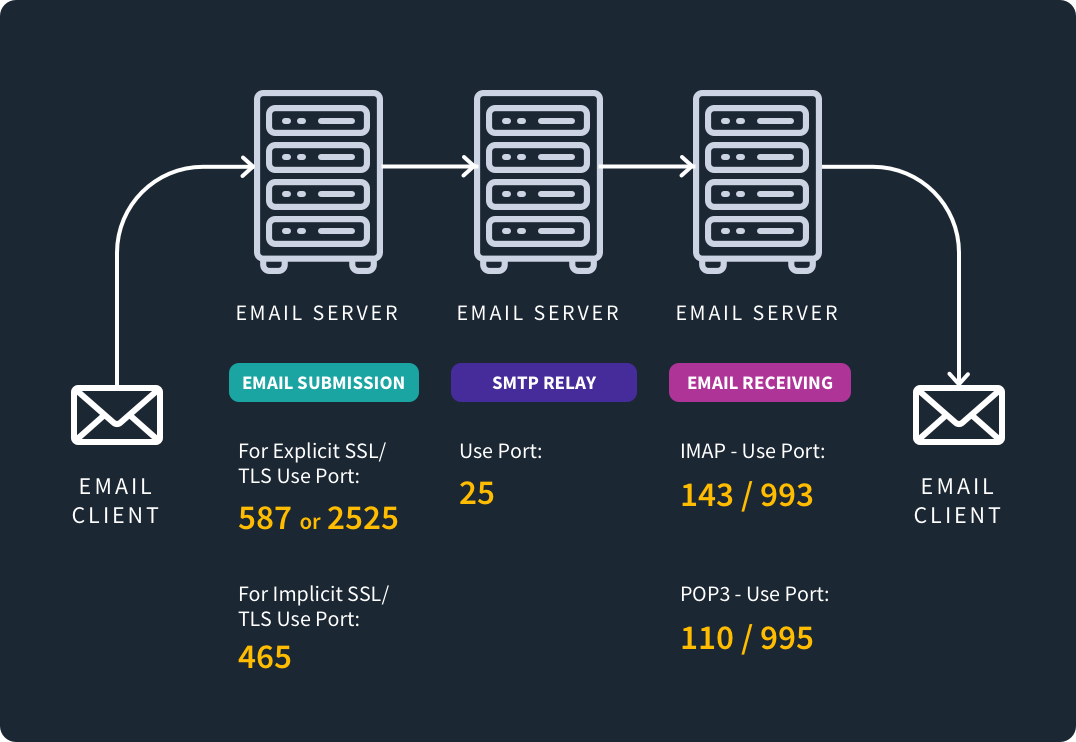
Now it’s time to dig even deeper into email protocols with a review of transfers, ports, and how they work.
Ports
Email ports, also known as message transfer agents, are required for SMTP emails. There are three ports: 25, 465, and 587.
Port 25 is the one that started it all. It was created in 1982. Attesting to its age, it allows for open relay support, which means spammers have gotten their grubby hands all over it. That said, it’s still good at SMTP relays or transferring emails between servers.
However, many cloud hosting providers and internet service providers don’t allow emails using port 25 to control spam, so reconsider using it.
Port 465 is a TLS port, meaning it uses TLS protocols when sending messages. Then there’s port 587, the new standard. This is your default port that works especially well with TLS encryption.
Transfers
As for transfers? Those refer to the data exchange that happens between servers and devices, such as computers. It can occur outside the limitations of software and hardware, making email more accessible.
Conclusion
Email protocols are critical for effective email marketing, as they determine if your emails go through or get blocked. Now that you have this useful knowledge, apply it to enhance your email campaign infrastructure moving forward!
EngageBay is an all-in-one marketing, sales, and customer support software for small businesses, startups, and solopreneurs. You get email marketing, marketing automation, landing page and email templates, segmentation and personalization, sales pipelines, live chat, and more.
Sign up for free with EngageBay or book a demo with our experts.
Frequently Asked Questions (FAQ)
1. What are the default port numbers for SMTP, IMAP, and POP3?
The default port number for SMTP is 587, 143 for IMAP, and 110 for POP3.
Understanding these default port numbers is crucial for the proper management and transfer of email messages across these protocols, ensuring efficient handling and access to email messages on servers through SMTP’s sending capabilities and IMAP’s advanced features like searching and organizing.
2. How can I check if my email authentication is set up correctly?
Review your email settings. You can also review the message headers in email services like Gmail. Open the email, click the header marked Authentication Results, and look for dkim=pass and/or spf=pass.
3. What’s the difference between SSL and TLS in email security?
SSL came first, with TLS building upon it to offer top-level encryption that keeps prying eyes out.
4. Is IMAP better than POP3 for email marketing purposes?
Yes, especially if you have a multi-person email marketing team. POP3 is designed more for email accounts where you use one device to check messages, whereas IMAP supports email syncing and management for more than one device.
5. How often should I review and update my email protocol settings?
Plan to update your settings for protocols every couple of months to ensure they’re up-to-date and your inbox remains secure.
6. What should I do if my emails are not being delivered properly?
First, check that your email protocol hasn’t blocked your message.
If not, then determine whether you got a soft or hard bounce. A soft bounce usually requires waiting a while and trying again, whereas a hard bounce might be due to issues with the recipient’s server or yours.
For example, your ISP might be blocking your emails because of a poor sender reputation.