Every day, 162 billion spam emails go out, making up 49% (ALMOST HALF) of all emails sent.
Some of these email spam contain harmful content, malware, ransomware, viruses, and phishing scams, posing a significant threat to the business. Email spam management is crucial, especially for small businesses, as they have a lot to lose from:
- A data breach in the only PC they’re operating from
- A scam that puts the only business account they’re managing financials from
If you want to understand what a spam email is and how to get rid of it, this article is for you. We’ve outlined:
- How to recognize different types of email spam
- How to set up spam filters
- What to do when spam bypasses filters
- Do’s and don’t for safe email practices
And more insights to bulletproof your small business email from unsolicited emails.
Table of Contents
What Is Email Spam?
Email spam, also called spam email or junk email, is an unsolicited message you receive in your mailbox. Most spam emails have a commercial purpose. However, spam can often have a malicious intent to infect computers, get access to the system, and steal your business’ money.
Spammers usually gather email addresses using spambots, a type of automation software. They may also purchase bulk email addresses illegally from other websites and forums.
Why Small Businesses Should Be Very Careful
Every year, about 73% of small businesses get attacked online, commonly by phishing scams. These scams can hurt your small business. Depending on the type and amount of stolen data, they could cost you massively.
The Internet Crime Complaint Center (IC3) reported more than $50 billion in losses worldwide caused by business email compromises between 2013 and 2022. Business Email Compromise (BEC), or Email Account Compromise, is a complex spam email scam that attacks businesses and people asking for legal money transfers through email spam. BEC involves hackers pretending to be someone the business trusts, like a company administrator, and asking for money.
For example, Treasure Island, a small homeless charity from San Francisco, lost $625,000 in a BEC fraud when hackers pretended to be the Executive Director and altered the instructions for a wire transfer in an invoice.
These email scams often cost businesses between $250 and $984,855, averaging $30,000. These numbers are especially staggering for small companies that may not have the financial reserves to sustain such phishing attacks. In addition to monetary costs, BEC can result in malicious email spam under your business name, which can cause reputational damage, customer loss, and even lawsuits.
As a small business, you and your employees are often more vulnerable to phishing emails as you might not have cybersecurity defenses like bigger organizations. Therefore, you and your company must deal with spam emails cautiously.
Related article: All The Email Spam Words You Should Avoid in Your Marketing
Learn How To Recognize Different Types of Email Spam
There are various kinds of spam emails you’ll encounter, and the following types are the most common.
Spam commercial advertisements
Usually, you automatically get on a business’s mailing list when you purchase something from their website and provide your email address. These emails are generally harmless but can be annoying if they flood your email inboxes.
Tip #1: Look for the unsubscribe link in the footer and click it to stop receiving unsolicited commercial emails from a certain business.
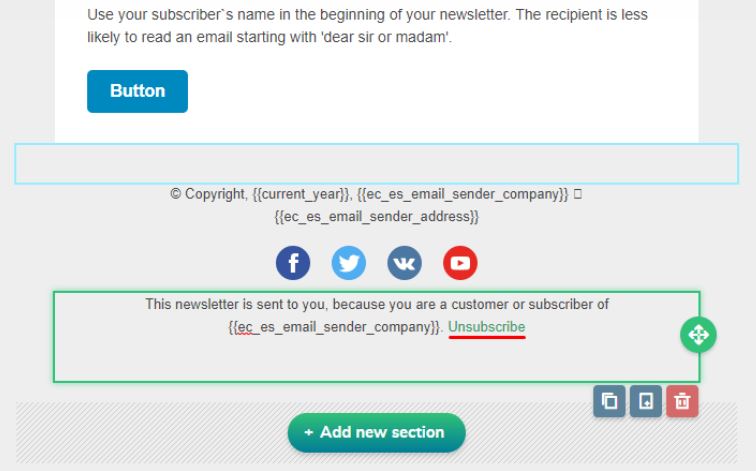
If you’re still receiving spam commercial advertisements from the same sender, go to your email preferences and apply email filters to send emails from the sender’s address into spam.
Fake antivirus warnings
Email spam using fake antivirus alerts is common. In this type of spam, the email informs you of a virus on your computer — a lie! Then, it offers an antivirus scan as a remedy.
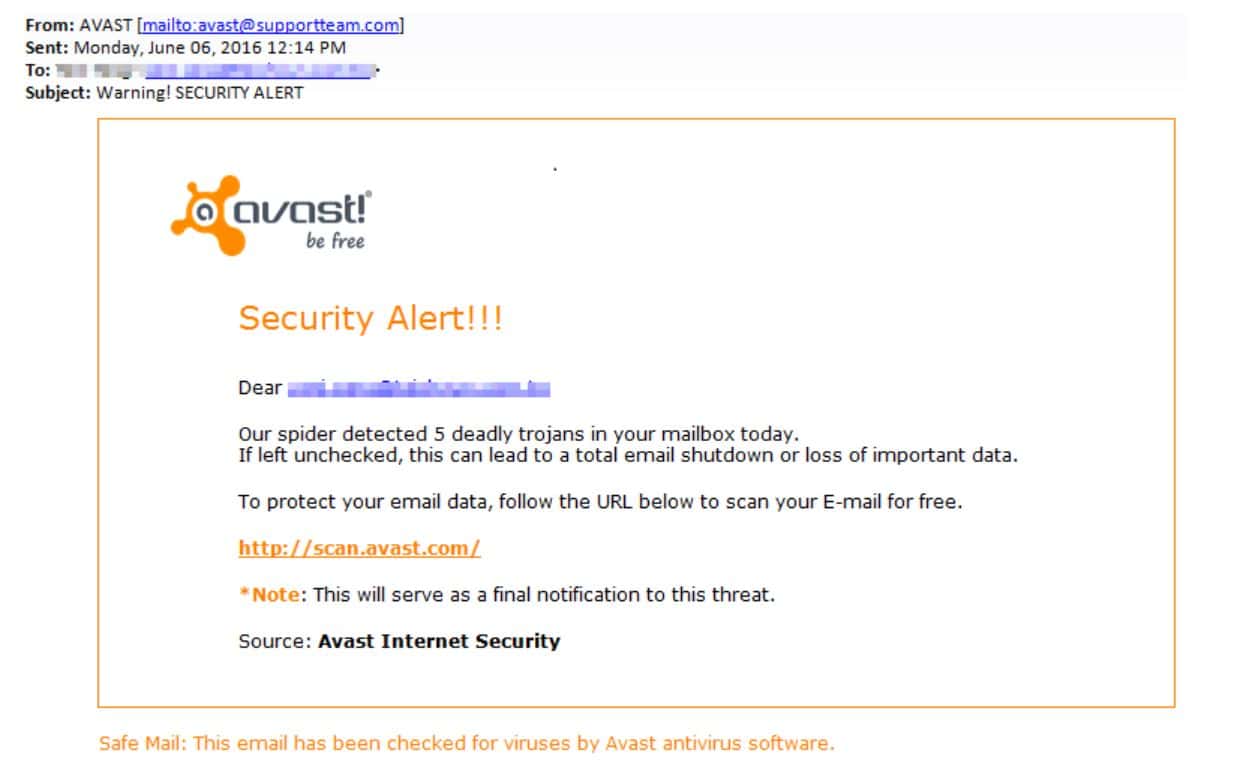
When you click the link, you get caught in a trap. It will install malware or give the hacker access to your system.
Tip #2: Don’t ever click on an unknown email link. If you have any reason to believe a virus may be on your computer, safeguard your system by pursuing genuine cybersecurity software solutions.
Sweepstakes winners
Did you get a random email claiming you’ve won a prize and you just need to pay a small amount to enter the competition? Or, even better, simply claim it by clicking on a link?
Beware! That’s a sweepstakes winner email spam! Sweepstakes, random prizes, and giveaways are the most common subjects of spam emails.

Tip #3: Avoid responding with personal details or clicking on links in an unsolicited email from unknown senders.
Email spoofing
This type of email spam is very dangerous because spammers impersonate legitimate businesses you may trust, such as banks and employers. In fact, after sweepstakes, job opportunities and banking-related fraud are the second and third most prevalent types of spam emails, reported by 36.3% and 34.6% of people, respectively.
Email spoofing includes using the identical language and logos of these. Spammers often ask for personal information, send malicious files or links, or even request money.
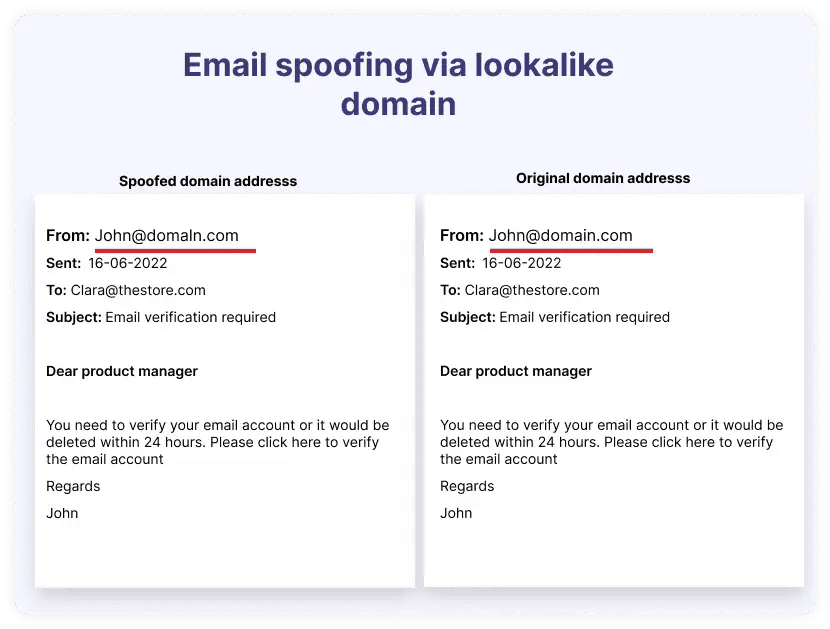
Tip #4: Verify the sender’s identity by looking at the email’s “From” line. Hackers may use characters that mimic real letters to make the email seem to have come from a known and trusted source (like the example above). If you have any doubts, don’t respond or click on links. Contact the business directly to make sure the email is legitimate.
Money scams
These types of email spam target naive people who fall for sending money to the sender in return for a promise. Take the Nigerian prince money scams, for example, where scammers often ask for sensitive financial information or a small sum of money in exchange for monetary rewards.
Another common money scam involves seeking donations. The sender tells a tale about how they need money for something bad that happened in their family or to them.
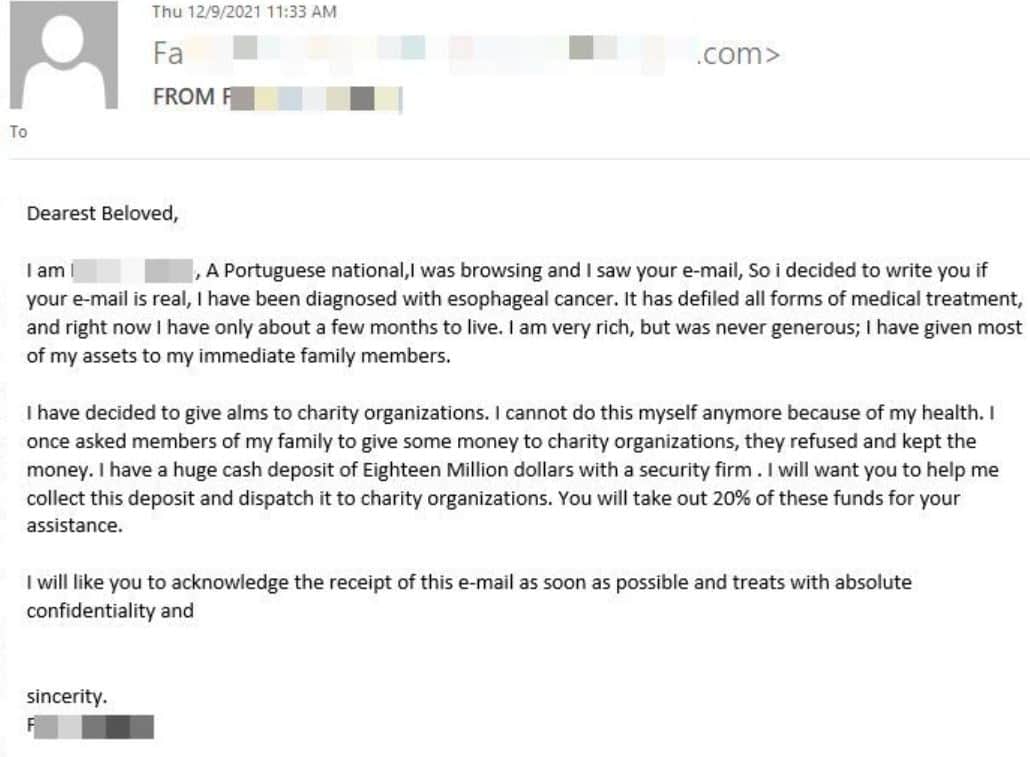
Tip #5: Always be extremely careful when sending money to an individual asking for it via email.
Subscription spams
This type of email spam targets the recipient by claiming a subscription they’ve never signed up for. The hacker asks the recipient to pay or cancel the subscription. However, the hacker enters the system once the recipient clicks on links.

Tip #6: Be wary of such spam emails, even if they seem to have originated from a company where you do business. To verify whether the email is legitimate, hover your cursor over the links to check if they go to a different or false website. Instead of visiting the email’s links, go straight to the company’s website and verify the status of your account.
Some additional tips
Tip #7: Be wary of urgency or fear used in the email with words
One common trend in phishing emails is scaring or rushing people to take action. Attackers could include messages in the subject line like “Your account is locked” or “Suspicious log-in activity.” People who get these emails or links get scared, which leads them to open the spam in haste.
Tip #8: Check for spammy subject lines
Read the subject line before you open the email. It’s likely to be spam if it excitingly persuades you to open it with subjects like sales or business possibilities, novel treatments, requesting money or personal details, a never-heard-of subscription, etc.
Tip #9: Spot the typos
Attackers use typos in their spam to avoid being caught by spam tools. For example, PayPal looks like ‘Paypal’ or Adobe becomes ‘Aclobe’, making us think the email is real. However, trusted brands would never make such mistakes in their email.
Tip #10: Stay away from stuff that’s too good to be true
Sometimes, spam emails say crazy things, like “download this link to get a lot of money RIGHT NOW.” These phishing emails aim to get you to give them your information. Just stay away from emails making such outlandish promises.
Tip #11: Enable spam filters
The last and most basic tip for individuals and small businesses is to ensure their spam filters are on! Most email providers have a built-in spam filter, which you simply need to ensure is on. It automatically identifies spam and keeps suspicious unsolicited email messages out of your inbox.
Wondering how spam filters work? Let’s see.
Read also: Top Tools & Strategies to Improve Email Deliverability Rates
Understanding Spam Filters
Spam filters detect potentially harmful and unwanted emails sent by spammers. They are a great way to safeguard your business email inboxes against unsolicited emails made to trick users. Different spam filters work in different ways to keep potential spam out of your inbox. Most business solutions use a layered approach that combines numerous filter types.
Listed below are some of the most prevalent kinds of spam filters.
Content or text-based spam filters
Content or text-based spam filters analyze the text within an email to determine spam. They scan for words related to money, such as “discount,” “free,” or “hurry.” They can also analyze emails for any vulgar or inappropriate language. There should be several instances of such a word to trigger the filter.
Blacklist filters
These filters retain a list of “spammy” IP addresses that are regularly updated to include old and new spammers. They filter any unwanted email coming from a spam-listed sender’s address. However, it’s common for spammers to use multiple email addresses. If a spammer uses any email addresses that aren’t listed, their unsolicited messages may still pass through the spam list until it is updated.
Whitelist filters
Only emails sent by verified senders will be allowed via whitelist filters. This filter helps you be sure that you will not get unsolicited messages from unknown senders. This filter works in tandem with blacklist filters to prevent genuine email addresses, such as those of frequent contacts, from accidentally being marked as spam.
Header and metadata filters
These filters look at an email’s header and metadata to determine whether it originated from a suspicious source. They look for spammers’ typical domain names, IP addresses, and subject lines. The header may also include details that show this email is one of several sent simultaneously to pre-arranged groups of people.
Language filters
Spammers often target individuals in foreign countries. Therefore, the email may contain a foreign language. These filters tag such emails as spam, considering most users will only be interested in receiving emails in their standard languages. However, customers or business contacts from other countries may receive legitimate messages filtered as spam. As a result, users may need a reminder to check their spam folder to receive communication.
Rule-based filters
You can set rules in different email services for built-in spam filters to scan all the emails you receive. For example, you can use Gmail rules to automatically report spam when email content or sources satisfy one of the criteria in your Gmail account. You may also configure rules to filter certain phrases or words in the header or block certain sender addresses or names to filter suspicious emails.
Bayesian filter
Bayesian filters learn from the unwanted messages you mark spam and adjust their rules appropriately. All future emails that attempt to reach your inbox will be subject to these rules.
How spam filters use machine learning and algorithms
Some spam filters improve protection by precisely targeting junk email using machine learning insights. Let’s see how they automatically send spam into junk.
- Learning from data: Machine learning models use massive email datasets that include both spam messages and valid email messages.
- Use of algorithms: Artificial neural networks (ANN), Naïve Bayes algorithm, and a decision tree-based algorithm learn spam email trends and traits, such as malicious links, the behavior of other spammers, and specific keywords and phrases to recognize spam.
- Prediction: Based on its training, the model can make predictions about the likelihood of new spam from incoming mail.
- Constant development: These models learn and adjust to new kinds of spam as they gather more data, increasing their effectiveness over time.
Read more: How To Avoid Spam Filters For Better Email Deliverability
How to Set Up Spam Filters?
Depending on your email provider, you can set up a custom spam filter from settings. Here’s how you can add custom spam filters to your Gmail account:
- Sign in to Google Admin Console using the administrator account.
- Navigate to Menu and then Apps. Then go to Google Workspace and click on Spam, Phishing, and Malware under Gmail.
- Choose an organizational unit on the left.
- Go to Spam and choose Configure or Add another rule.
- Give a unique name to the setting in the Add setting
- Select your option for spam filtering.
- Click Save at the bottom.
Note: The changes may take up to 24 hours to implement.
Here’s a list of all spam filtering options:
| Option for setting | What it means? |
| Be more aggressive when filtering spam | Expect an increase in incoming messages identified as spam and sent to the receivers’ spam folders. |
| Put spam in administrative quarantine | Instead of going to the recipient’s spam folder, messages go to email quarantine for evaluation. Before messages are released from quarantine and sent to their intended recipients, they are re-screened by Gmail’s spam filters. |
| Bypass spam filters for internal senders | Your organization’s internal emails will get past Gmail’s spam filters. Your subdomains, even those not hosted by Google, will still be considered internal communications if they send an authenticated message. |
| Bypass spam filters for messages from senders or domains in selected lists | Gmail does not block spam messages from domains or addresses on an authorized senders list. |
| Bypass spam filters and hide warnings for messages from senders or domains in selected lists | Gmail does not block spam messages from domains or addresses on an authorized senders list. Notifications about potentially malicious files or links are also not shown for these messages. |
| Bypass spam filters and hide warnings for all messages from internal and external senders | Gmail’s spam filters do not filter out inbound mail, and there are no alerts about potentially malicious links or files. |
What To Do When Spam Bypasses Filters?
You may easily report email spam with most email services. Follow these steps to report spam emails on different email providers, such as Apple Mail, Google, and Outlook.
Reporting spam emails on Apple Mail
To send unwanted emails to the Apple Mail junk mail folder, follow these three steps:
Step 1: Click on the unsolicited email messages to select it.
Step 2: Choose the “Move to” option on the toolbar at the top.
Step 3: Click on “Junk” in the dropdown menu.
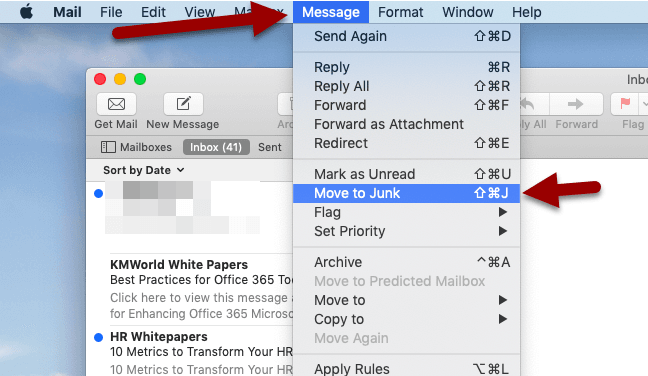
That’s it! You’ve cleared out your junk mail, and Apple Mail will learn from this action to move any junk email you receive in the future to a separate folder.
Reporting spam emails on Gmail
To send unwanted emails to the Gmail spam folder, follow these steps:
Step 1: Select all the unsolicited email messages by checking them.
Step 2: Choose the option “Report Spam” on the top toolbar that looks like an exclamation mark.
By reporting Spam, you teach Google spam filters to block similar messages from reaching your inbox in the future.
Reporting spam emails on Outlook
To mark a junk email on Outlook as spam, follow the steps below:
Step 1: Select all the unsolicited email messages by checking them.
Step 2: Choose the “Junk” option on the toolbar at the top.
Step 3: Click ” Report As Junk” or “Report As Phishing” as relevant in the dropdown menu.
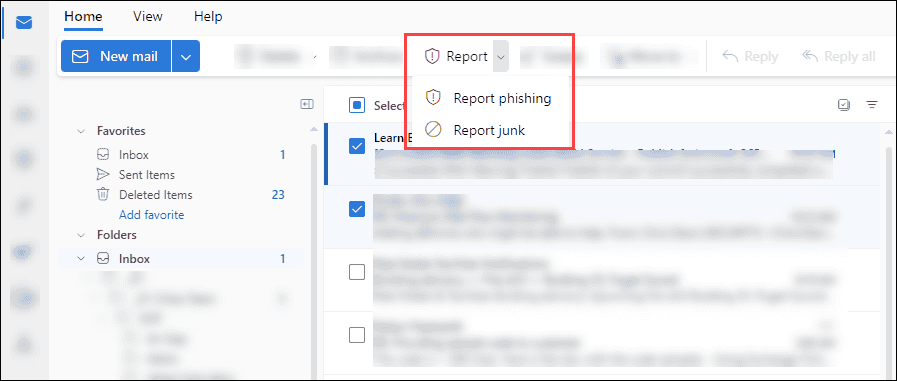
This step will forward your chosen email message to the junk folder and notify Outlook’s spam filters to help prevent future unsolicited email messages.
Do’s and Don’t For Safe Email Practices
Don’t: Display your business emails publicly on forums, social media platforms, or websites. Public availability makes it easy for spambots to harvest email addresses.
Do: Use a contact form or private chat instead.
Don’t: Give your business email addresses when asked for contact details online or signup forms.
Do: Check privacy policies and ensure the website is reputable.
Don’t: Click on suspicious links to avoid downloading malicious files.
Do: Verify unknown senders and validate their addresses.
Don’t: Click unfamiliar unsubscription links, as they could be malicious.
Do: Make sure that the promotional email comes from a legitimate sender.
Don’t: Use easy-to-guess and remember passwords for your email account.
Do: Create unique passwords and use multi-factor authentication to avoid compromising it.
Don’t: Keep your personal and business email accounts the same.
Do: Maintain separate email accounts for private and business use.
How To Secure Your Business’ Email Servers?
With growing cyber threats, a business must safeguard their email servers. You can protect the sensitive information of your business by setting up email servers according to standard authentication and verification protocols, such as:
- Sender Policy Framework (SPF): An online resource that lists validated IP addresses of your domain that are secure for sending messages.
- DomainKeys Identified Mail (DKIM): An encryption process that verifies the integrity of your email by adding a digital signature and ensuring it remains unaltered while in transit.
- Domain-based Message Authentication, Reporting & Conformance (DMARC): A protocol that verifies the sending domain to give another layer of protection in addition to the above protocols. It also offers XML reports to the specified servers that help determine the best way to implement email regulations.
Benefits of using authentication and verification protocols
You don’t want your domain listed as spam if you’re sending email newsletters for your business. It will affect your business’s reputation and shrink your customer pool. By employing the above authentication and verification protocols, you can:
- Build trust among your customers
- Safeguard your business from cyberattacks
- Build more leads with unhitched email marketing
Want to learn how to ensure your email marketing messages don’t land in customers’ spam folders? Read our article Avoiding The Spam Folder: An Intro To Email Deliverability.
Prepare Your Business To Fight Email Spam
You must implement an email security policy to protect your business and customers from spam. With a detailed outline beforehand, you can successfully enforce the policy in your business.
Use a policy template
Using a security policy template speeds up email security policy creation and ensures you don’t miss important components. Add company-specific practices, adapt rules to match the business environment, and include legal and regulatory requirements.
Get the policy-related email security setup in line
Get all your security settings, including spam filters, protocols, and access restrictions, in line with the policy requirements. Review security setups and update regularly to keep up with ever-changing threats.
User policy acknowledgment and agreement for employees
Getting employees to acknowledge and agree with user policy ensures everyone is on the same page about the email security policy. Reaffirm and update the policy regularly to help your staff always remember it.
Outline methods for incident response
Implementing the procedure as on record is crucial for efficiently handling and minimizing the consequences of malicious email spam.
Train your employees
Training sessions teach your employees to prevent modern cyber dangers by recognizing malicious links, files, and phishing patterns. Training should also review the company’s rules and processes for reporting spam emails and properly using company email.
Stay Compliant With Your Email Communications
If you stay in touch with your customers via email, you must strictly follow laws regulating email communication and spam to ensure email compliance. Since email is a major communication source amongst businesses and their clients to send and receive private information, email compliance protects it. Here’s why email compliance is important:
- It enforces consent to let the user decide when and how you use their data.
- It ensures that people retain the power to avoid unwanted messages and that companies follow ethical practices when sending marketing material via email.
- It plays an important role in preventing email spam, the spread of misleading information, scams, and cyber attacks.
Here are some key email compliance regulations that businesses implementing email marketing should know.
General Data Protection Regulation (GDPR ACT)
GDPR is an EU policy for information security that addresses data protection, including email marketing and spam rules. According to the legislation, data owners, not data storage companies, are EU citizens, meaning:
- You can’t send emails or use anyone’s data without opt-in consent
- You must delete your subscriber’s personal information if they ask
- You must keep all company data, communications, and audits secret and have strong IT security procedures
The Controlling the Assault of Non-Solicited Pornography And Marketing Act (CAN-SPAM ACT)
Like GDPR, CAN-SPAM specifies the conditions under which businesses may engage in email marketing. However, companies may send communications without opt-in consent, and recipients may opt out of receiving emails. Here is how to comply with CAN-SPAM:
- Don’t send content that may mislead readers
- Don’t use deceptive subject lines
- Make sure you mention that the email is promotional or an ad
- Must include a postal address
- Give an opt-out option and respect it
- Don’t track anyone’s email marketing campaigns
Canada’s Anti-Spam Legislation (CASL ACT)
By advocating for industry-leading practices in email marketing, CASL combats email spam and related issues. It enforces much more stringent rules on marketing, such as:
- Obtaining clear consent from email recipients
- Sending one-time double opt-in requests to those who haven’t provided explicit consent to email marketing
- Providing an option to unsubscribe and respecting it within 10 days
When you comply with email laws, you save yourself from getting marked as potential spam. Following these regulations builds trust among your customers, increasing their engagement with your brand.
Conclusion
Managing email spam is non-negotiable for small businesses, especially with increasing cyberattacks from hackers and spammers. After reading this article, you should be able to identify any spam email and eliminate it efficiently. Use spam filters to automate spam deletion and keep your inbox clean.
If you hope to implement a strong email marketing strategy for your business, use EngageBay to manage email campaigns, automate processes, and ensure your communications reach the right audience without hitting spam folders. Sign up today to get started for free!
FAQ
1. What exactly is considered ’email spam’?
Spam email is the mass mailing of unwanted, irrelevant, or otherwise improper communications delivered by email. Although spam emails usually have a business purpose, they may also be harmful and try to install malware, steal sensitive information, or scam the receiver.
2. How can I tell if an email is spam or legitimate?
There are several red flags you can look for to tell a spam email apart from legitimate ones, such as:
- Random messages from unknown senders
- Emails with language suggesting urgency or threats
- The email contains suspicious links or attachments
- Requests personal information or asks to send money
- Content full of spelling mistakes and grammatical errors
- Offers that are too good to be true
3. What are the immediate steps to take when I receive spam?
If you’re certain that you have received a spam email, take the following steps:
- Avoid opening any links or attachments
- Report spam or junk in your email provider to help it learn to filter future messages
- Reconfigure your email security settings
- Update your antivirus software for additional protection